Things I describe here are only to be used in a “lab/ctf” environment or on systems you have actually permission to try things out on.
Discovery
When playing around on HTB I ran into a strange port/service I hadn’t seen before. My nmap scan showed that port 50051 was active but “unknown”. Just out of curiosity opened a connection to it by using telnet after a while it timed out stating that its a HTTP/2 based service:
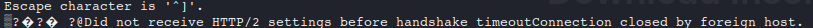
A quick Google search later it seemed to be a gRPC server. You can read more about it on their website gRPC.
Tools to interact with gRPC
As I hadn’t played around with gRPC previously I spent some time looking at tools and ways to interact with gRPC applications.
The options I found were:
- Writing python code using hints from the gRPC website
- grpcurl found on GitHub
- grpcui found on GitHub
- Postman
- Insomnia
After a quick look I ruled out writing Python code, as it seemed too much for a “simple CTF machine” and my current use case.
Next I took a look at Postman/Insomnia, their interface was similar and they could easily interact with the gRPC service but they were lacking some functionality to conveniently pentest the application.
Yes they were able to show what “Symbols” are available in the gRPC app, it they didn’t return some descriptive info/reflections properly at least in the app I was “hacking” which ended up for me looking at other tools.
grpcurl looked like a nice command line tool and was able to explore the app nicely:
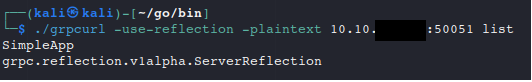
But it also didn’t reflect all the features/parameters of the application and was still lacking something I found that grpcui had!
Now we come to my favorite of the bunch and that got me past the finish line on my target machine – grpcui. What this tool does is give you a WebUI to access and interact with the backend gRPC application. Why this is good for “hacking and pentesting” is that this gives you the option of proxying the connection through BurpSuite and use other automation tools to interact with the gRPC service. The current version of grpcui had a “csrf token”, but it was a static value so you could indefinitely, so basically could be ignored.
Testing/”hacking” a gRPC application
So after having found a tool that seemed to suite my purpose I started poking and prodding at my target gRPC application using a web browser with the help of grpcui.
When starting grpcui it basically starts a little WebUI on localhost:”SomeRandomHighPort” which you should access via a web browser. Startup Example :
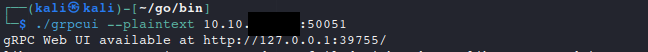
If you use the bind parameter to bind it to some IP address that differs from loopback(127.0.0.1) then your browser will gladly proxy your connections to Burp or ZAP. After that you can continue your “regular pentesting workflow” .
In my case after having poked and prodded at the app for a bit I found that it had a SQLi in it. So I opted to take the raw request from Burp and “unleashed” sqlmap on it and dumped the whole database. That contained a username and password combo in it I could use to access the box over SSH and “user flag claimed”.
Leave a Reply